The purpose of this cybersecurity budget template is to provide Canadian businesses with a structured approach to allocating their cybersecurity resources effectively. In today’s digital landscape, robust cybersecurity measures are critical to protecting sensitive information and maintaining business continuity. This template is tailored specifically to the financial and regulatory environment of Canada, ensuring that businesses can meet their security needs while complying with national regulations.
Overview of the Canadian Cybersecurity Landscape
The cybersecurity landscape in Canada is shaped by a dynamic mix of evolving threats and stringent regulatory requirements. Canadian businesses face a range of cyber threats, including ransomware attacks, phishing scams, and data breaches. Understanding these threats is crucial for effective budget planning.
- Current Trends and Threats: Cyber threats are continuously evolving, with attackers employing sophisticated techniques to exploit vulnerabilities. Businesses must stay informed about the latest trends to anticipate and mitigate potential risks.
- Regulatory Environment: Canada has established comprehensive regulations to protect personal data and ensure cybersecurity, such as the Personal Information Protection and Electronic Documents Act (PIPEDA) and the Canadian Anti-Spam Legislation (CASL). Compliance with these regulations is mandatory for businesses operating in Canada.
- Key Stakeholders and Resources: Various government agencies, industry bodies, and cybersecurity organizations provide valuable resources and support to businesses. Key stakeholders include the Canadian Centre for Cyber Security (CCCS), the Canadian Internet Registration Authority (CIRA), and the Canadian Cyber Threat Exchange (CCTX).
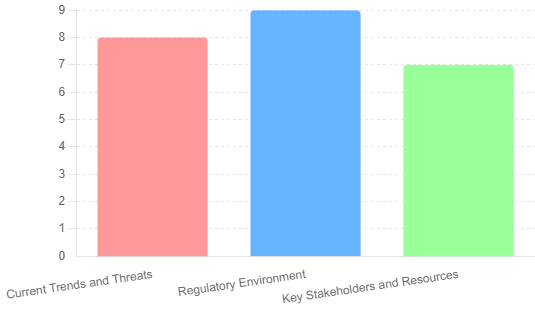
Here is a graph showcasing the current Canadian Cybersecurity Landscape, highlighting the assessment levels of current trends and threats, regulatory environment, and key stakeholders and resources. The values are rated on a scale from 1 to 10, providing a visual representation of the critical aspects of cybersecurity in Canada
Understanding Cybersecurity Needs
1. Risk Assessment
Effective cybersecurity budgeting starts with a thorough risk assessment to identify and evaluate potential threats and vulnerabilities within the organization.
- Identifying and Evaluating Risks: Businesses should conduct comprehensive assessments to pinpoint areas of potential risk. This includes evaluating network security, software vulnerabilities, and employee practices.
- Impact Analysis on Business Operations: Determine the potential impact of identified risks on various aspects of business operations, including financial loss, reputational damage, and operational downtime.
- Prioritizing Threats Based on Potential Impact: Rank threats by their potential impact and likelihood, allowing businesses to focus resources on mitigating the most significant risks first.
This table includes columns for identifying risks, evaluating their impact and likelihood, and prioritizing them based on their overall risk score.
| Risk ID | Risk Description | Vulnerability | Potential Impact | Likelihood | Impact Score | Likelihood Score | Overall Risk Score | Mitigation Strategy | Responsible Party | Notes |
|---|---|---|---|---|---|---|---|---|---|---|
| 1 | Phishing Attack | Employee emails | High (Data breach) | Likely | 5 | 4 | 20 | Employee training, email filtering | IT Security Team | Regular training sessions |
| 2 | Ransomware Infection | Network systems | Critical (Operational downtime) | Possible | 5 | 3 | 15 | Regular backups, anti-malware software | IT Security Team | Test backups monthly |
| 3 | Data Theft | Customer database | High (Loss of customer trust) | Unlikely | 4 | 2 | 8 | Encryption, access controls | Data Protection Officer | Regular audits |
| 4 | Insider Threat | Internal staff | Medium (Data loss) | Possible | 3 | 3 | 9 | Access restrictions, monitoring | HR & IT Security Team | Perform background checks |
| 5 | DDoS Attack | Web servers | High (Website downtime) | Likely | 4 | 4 | 16 | DDoS protection services | IT Infrastructure Team | Monitor traffic patterns |
| 6 | Software Vulnerability | Legacy software | Critical (System compromise) | Possible | 5 | 3 | 15 | Regular patching, vulnerability scans | IT Operations Team | Schedule monthly updates |
Table Explanation
- Risk ID: A unique identifier for each risk.
- Risk Description: A brief description of the identified risk.
- Vulnerability: The specific vulnerability that could be exploited.
- Potential Impact: The potential consequences if the risk is realized.
- Likelihood: The probability of the risk occurring.
- Impact Score: A numerical value representing the severity of the impact (e.g., 1 to 5 scale, where 5 is highest).
- Likelihood Score: A numerical value representing the probability of occurrence (e.g., 1 to 5 scale, where 5 is highest).
- Overall Risk Score: Calculated by multiplying the Impact Score by the Likelihood Score.
- Mitigation Strategy: The planned actions to mitigate the risk.
- Responsible Party: The individual or team responsible for managing the risk.
- Notes: Additional comments or observations.
This table helps businesses systematically assess their cybersecurity risks and prioritize mitigation efforts based on the potential impact and likelihood of each risk.
2. Compliance Requirements
Understanding and adhering to regulatory requirements is essential for Canadian businesses to avoid legal penalties and build customer trust.
- Overview of Relevant Regulations (PIPEDA, CASL): Familiarize with key regulations such as PIPEDA, which governs the handling of personal information, and CASL, which addresses electronic communications and anti-spam measures.
- Industry-Specific Compliance (e.g., Healthcare, Finance): Different industries have specific compliance requirements. For instance, healthcare organizations must comply with PHIPA (Personal Health Information Protection Act), while financial institutions may need to adhere to guidelines from the Office of the Superintendent of Financial Institutions (OSFI).
- Best Practices for Maintaining Compliance: Implement best practices such as regular audits, employee training, and adopting industry-standard security frameworks (e.g., ISO 27001, NIST).
This table includes columns for identifying regulations, describing requirements, evaluating their applicability and impact, and planning compliance actions.
| Regulation | Requirement Description | Applicable Business Units | Impact on Business | Compliance Status | Actions Required | Deadline | Responsible Party | Notes |
|---|---|---|---|---|---|---|---|---|
| PIPEDA | Protect personal information | All departments handling personal data | High (Legal and reputational risk) | Partially Compliant | Implement data protection policies, conduct employee training | 2024-12-31 | Data Protection Officer | Regular audits needed |
| CASL | Anti-spam measures | Marketing, Sales | Medium (Fines, customer trust) | Non-Compliant | Update email marketing practices, obtain explicit consent | 2024-09-30 | Marketing Manager | Review consent forms |
| PHIPA | Protect health information | Healthcare, HR | High (Legal penalties) | Fully Compliant | Maintain compliance, regular staff training | Ongoing | Compliance Officer | Annual review required |
| GDPR | Data protection for EU citizens | Sales, Customer Service | Medium (Global reach) | Non-Compliant | Update privacy policies, appoint Data Protection Officer | 2024-06-30 | Legal Department | Monitor for updates |
| ISO 27001 | Information security management | IT, Operations | High (Security and business continuity) | Partially Compliant | Implement ISMS, conduct internal audits | 2024-11-30 | IT Security Team | Certification required |
| SOX | Financial reporting controls | Finance, Accounting | Medium (Financial accuracy) | Fully Compliant | Maintain controls, regular audits | Ongoing | CFO | Quarterly review |
| HIPAA | Health information privacy | Healthcare, HR | High (Legal penalties) | Non-Compliant | Develop privacy and security policies, train staff | 2024-08-31 | HR Manager | Immediate action required |
| CCPA | Consumer data privacy | Sales, Marketing | Medium (Consumer trust, fines) | Partially Compliant | Update privacy notices, provide opt-out options | 2024-07-31 | Customer Service Manager | Monitor compliance |
Table Explanation
- Regulation: The specific regulation or standard.
- Requirement Description: A brief description of the compliance requirement.
- Applicable Business Units: The business units affected by the requirement.
- Impact on Business: The potential impact of non-compliance on the business.
- Compliance Status: The current compliance status (e.g., Fully Compliant, Partially Compliant, Non-Compliant).
- Actions Required: The actions needed to achieve or maintain compliance.
- Deadline: The deadline for completing the compliance actions.
- Responsible Party: The individual or team responsible for ensuring compliance.
- Notes: Additional comments or observations.
This table helps businesses systematically assess their compliance requirements, prioritize actions, and ensure that all regulatory obligations are met in a timely manner.
3. Business-Specific Considerations
Each business has unique cybersecurity needs based on its size, industry, and existing infrastructure.
- Company Size and Industry: Small and medium-sized enterprises (SMEs) may have different budget constraints and risk profiles compared to larger corporations. Industry-specific threats and regulatory requirements must also be taken into account.
- Existing Cybersecurity Infrastructure: Assess the current state of the organization’s cybersecurity measures, including technology, policies, and personnel. Identify gaps and areas for improvement.
- Future Growth and Technology Adoption: Consider future business growth and planned technology adoption. Budgeting for cybersecurity should be flexible enough to accommodate new technologies and evolving threats.
This table includes columns for assessing various aspects of the business, evaluating their current state, identifying gaps, and planning necessary actions.
| Business Aspect | Current State | Evaluation | Gaps Identified | Actions Required | Responsible Party | Deadline | Notes |
|---|---|---|---|---|---|---|---|
| Company Size | Small (50 employees) | Adequate | Limited cybersecurity staff | Hire additional staff, provide training | HR Manager | 2024-08-31 | Prioritize critical roles |
| Industry | Retail | High Risk | High volume of sensitive customer data | Implement robust data protection measures | IT Security Team | 2024-07-31 | Focus on customer data security |
| Existing Cybersecurity Infrastructure | Basic firewall and antivirus software | Inadequate | Lack of advanced threat detection systems | Invest in advanced security solutions | IT Manager | 2024-09-30 | Evaluate vendors for solutions |
| Future Growth Plans | Expanding to online sales | Significant | Increased attack surface | Develop and implement e-commerce security | E-commerce Director | 2024-10-31 | Plan for scalability |
| Technology Adoption | Adopting cloud services | Moderate | Limited cloud security measures | Implement cloud security policies and tools | Cloud Services Manager | 2024-11-30 | Conduct staff training |
| Regulatory Compliance | Compliant with PIPEDA | Adequate | Potential gaps in ongoing compliance | Conduct regular compliance audits | Compliance Officer | Ongoing | Stay updated on regulation changes |
| Employee Training | Basic cybersecurity awareness | Inadequate | Insufficient training programs | Develop comprehensive training programs | Training Coordinator | 2024-08-15 | Include phishing simulations |
| Budget Allocation | $100,000 annually | Limited | Insufficient for comprehensive security | Reevaluate and increase budget allocation | CFO | 2024-07-31 | Align budget with risk profile |
| Vendor Management | Basic vetting process | Moderate | Lack of continuous monitoring | Implement vendor security assessment process | Procurement Manager | 2024-08-31 | Include third-party audits |
| Incident Response Plan | Outdated and not tested | Inadequate | Lack of regular updates and drills | Update plan, conduct regular drills | Incident Response Team | 2024-09-15 | Schedule bi-annual reviews |
Table Explanation
- Business Aspect: The specific aspect of the business being evaluated.
- Current State: The current status or condition of the aspect.
- Evaluation: An assessment of the adequacy or risk level of the current state.
- Gaps Identified: Specific shortcomings or areas needing improvement.
- Actions Required: Necessary steps to address identified gaps.
- Responsible Party: The individual or team responsible for implementing the actions.
- Deadline: The deadline for completing the actions.
- Notes: Additional comments or observations.
This table helps businesses systematically evaluate their specific considerations, identify gaps in their cybersecurity posture, and plan targeted actions to enhance their overall security.
Budgeting Principles
1. Key Budget Categories
Understanding the key categories where cybersecurity funds should be allocated is essential for creating an effective budget. These categories ensure a comprehensive approach to cybersecurity, covering all necessary areas.
- Personnel
- Salaries and Benefits: Allocate funds for hiring and retaining skilled cybersecurity professionals. This includes competitive salaries, benefits, and bonuses.
- Training and Certifications: Budget for ongoing training and certifications to keep staff updated on the latest cybersecurity practices and technologies.
- Recruitment and Retention Strategies: Invest in strategies to attract and retain top cybersecurity talent, including recruitment campaigns and retention bonuses.
- Technology
- Security Software: Allocate funds for purchasing and maintaining security software such as antivirus programs, firewalls, and Security Information and Event Management (SIEM) systems.
- Hardware: Invest in secure hardware, including encrypted devices, secure servers, and reliable network infrastructure.
- Network Security: Budget for network security measures such as Virtual Private Networks (VPNs), secure routers, and intrusion detection systems.
- Services
- Consulting and Advisory Services: Engage external consultants and advisory services for expert guidance on cybersecurity strategy and implementation.
- Managed Security Services: Consider outsourcing certain security functions to Managed Security Service Providers (MSSPs) to leverage their expertise and resources.
- Incident Response and Forensic Analysis: Allocate funds for incident response services and forensic analysis to quickly and effectively respond to security incidents.
- Compliance and Auditing
- Regular Security Audits and Assessments: Budget for regular audits and assessments to ensure compliance with relevant regulations and standards.
- Compliance Certifications: Invest in obtaining and maintaining compliance certifications such as ISO 27001, SOC 2, and other industry-specific certifications.
- Legal and Regulatory Consultations: Allocate funds for legal consultations to navigate the complex regulatory landscape and ensure compliance.
2. Strategic Allocation of Funds
Allocating funds strategically ensures that resources are used efficiently to maximize cybersecurity effectiveness.
- Balancing Between Proactive and Reactive Measures
- Proactive Measures: Invest in preventive measures such as security training, threat intelligence, and regular system updates to prevent incidents from occurring.
- Reactive Measures: Allocate funds for incident response, forensic analysis, and disaster recovery to quickly address and mitigate the impact of security incidents.
- Investing in Prevention vs. Response
- Prevention: Focus on measures that reduce the likelihood of incidents, such as employee training, access controls, and regular security updates.
- Response: Ensure adequate funding for rapid response capabilities, including incident response teams, forensic tools, and recovery plans.
- Ensuring Continuous Improvement and Flexibility
- Continuous Improvement: Regularly review and update the cybersecurity budget to adapt to changing threats and technologies.
- Flexibility: Maintain flexibility in the budget to respond to emerging threats and unexpected incidents, allowing for quick reallocation of funds as needed.
This table includes various budget categories, specific items within those categories, estimated costs, actual costs, and notes for detailed planning and tracking.
| Category | Item | Estimated Cost | Actual Cost | Variance | Notes |
|---|---|---|---|---|---|
| Personnel | |||||
| Salaries and Benefits | $200,000 | Competitive salaries for staff | |||
| Training and Certifications | $30,000 | Ongoing training programs | |||
| Recruitment and Retention Strategies | $15,000 | Recruitment campaigns, bonuses | |||
| Technology | |||||
| Security Software | $50,000 | Antivirus, firewalls, SIEM | |||
| Hardware | $40,000 | Secure servers, encrypted devices | |||
| Network Security | $25,000 | VPNs, secure routers | |||
| Services | |||||
| Consulting and Advisory Services | $20,000 | External cybersecurity consultants | |||
| Managed Security Services | $45,000 | MSSPs | |||
| Incident Response and Forensic Analysis | $35,000 | Response and analysis services | |||
| Compliance and Auditing | |||||
| Regular Security Audits and Assessments | $15,000 | Regular compliance checks | |||
| Compliance Certifications | $10,000 | ISO 27001, SOC 2 | |||
| Legal and Regulatory Consultations | $10,000 | Legal advice on compliance | |||
| Incident Response | |||||
| Incident Response Planning and Drills | $20,000 | Response planning and testing | |||
| Backup and Disaster Recovery Solutions | $30,000 | Backup systems, recovery plans | |||
| Insurance and Liability Coverage | $20,000 | Cybersecurity insurance | |||
| Total | $565,000 |
Table Explanation
- Category: The main areas of the cybersecurity budget.
- Item: Specific items or services within each category.
- Estimated Cost: The projected cost for each item.
- Actual Cost: The actual cost incurred (to be filled in during or after implementation).
- Variance: The difference between estimated and actual costs.
- Notes: Additional comments or observations about each item.
This table helps businesses plan, track, and adjust their cybersecurity budgets effectively, ensuring all necessary areas are covered and funds are allocated efficiently.
Detailed Budget Template
1. Personnel Costs
Personnel costs are critical for maintaining a skilled and effective cybersecurity team. This section outlines the necessary expenses related to hiring, training, and retaining cybersecurity professionals.
| Item | Description | Estimated Cost | Actual Cost | Variance | Notes |
|---|---|---|---|---|---|
| Salaries and Benefits | Competitive salaries and benefits for cybersecurity staff | $200,000 | Ensure market-competitive salaries | ||
| Training and Certifications | Ongoing training programs and certifications | $30,000 | Include certifications like CISSP | ||
| Recruitment and Retention Strategies | Recruitment campaigns and retention bonuses | $15,000 | Attract and retain top talent |
2. Technology Investments
Investing in the right technology is vital for a robust cybersecurity infrastructure. This section includes costs for security software, hardware, and network security.
| Item | Description | Estimated Cost | Actual Cost | Variance | Notes |
|---|---|---|---|---|---|
| Security Software | Antivirus, firewalls, SIEM systems | $50,000 | Annual subscription fees | ||
| Hardware | Secure servers, encrypted devices | $40,000 | Include backup and recovery devices | ||
| Network Security | VPNs, secure routers, intrusion detection systems | $25,000 | Ensure high availability |
3. Services and External Support
External services and support can enhance the effectiveness of an internal cybersecurity team. This section includes costs for consulting services, managed security services, and incident response.
| Item | Description | Estimated Cost | Actual Cost | Variance | Notes |
|---|---|---|---|---|---|
| Consulting and Advisory Services | External cybersecurity consulting | $20,000 | Strategic guidance and planning | ||
| Managed Security Services | Outsourced security monitoring and management | $45,000 | Continuous monitoring services | ||
| Incident Response and Forensic Analysis | Response and forensic services | $35,000 | Rapid response capabilities |
4. Compliance and Regulatory Costs
Compliance with regulations is mandatory and requires regular audits, certifications, and legal consultations. This section includes the related costs.
| Item | Description | Estimated Cost | Actual Cost | Variance | Notes |
|---|---|---|---|---|---|
| Regular Security Audits and Assessments | Regular compliance checks | $15,000 | Annual assessments | ||
| Compliance Certifications | ISO 27001, SOC 2 certifications | $10,000 | Certification costs | ||
| Legal and Regulatory Consultations | Legal advice on compliance | $10,000 | Legal fees |
5. Incident Response and Recovery
Effective incident response and recovery plans are essential for minimizing the impact of security incidents. This section includes costs for planning, testing, and implementing recovery solutions.
| Item | Description | Estimated Cost | Actual Cost | Variance | Notes |
|---|---|---|---|---|---|
| Incident Response Planning and Drills | Response planning and testing | $20,000 | Conduct regular drills | ||
| Backup and Disaster Recovery Solutions | Backup systems, recovery plans | $30,000 | Ensure data integrity | ||
| Insurance and Liability Coverage | Cybersecurity insurance | $20,000 | Cover potential liabilities |
V. Monitoring and Evaluation
1. Performance Metrics
To ensure the effectiveness of the cybersecurity budget, it is essential to establish performance metrics and regularly monitor them. This helps in evaluating the success of the implemented strategies and making necessary adjustments.
| Metric | Description | Target | Current Status | Notes |
|---|---|---|---|---|
| Incident Response Time | Average time to respond to security incidents | < 1 hour | Track response efficiency | |
| Compliance Audit Score | Score from regular compliance audits | 95%+ | Maintain high compliance levels | |
| Employee Training Completion | Percentage of employees completing training | 100% | Ensure all employees are trained | |
| Number of Security Incidents | Total number of reported security incidents | < 5 per year | Aim to minimize incidents | |
| System Uptime | Percentage of time systems are operational and secure | 99.9% | Ensure high availability | |
| Budget Utilization Rate | Percentage of allocated budget used effectively | 100% | Optimize resource usage |
2. Review and Adjustment Process
Regular review and adjustment of the cybersecurity budget ensure that it remains aligned with the business needs and evolving threat landscape. This process includes periodic reviews to assess the effectiveness of budget allocation and make necessary changes.
| Review Frequency | Description | Next Review Date | Responsible Party | Notes |
|---|---|---|---|---|
| Quarterly Review | Regular review of budget allocations | Quarterly | CFO | Adjust based on performance metrics |
| Annual Review | Comprehensive review of overall cybersecurity budget | Annually | CIO | Align with strategic business goals |
| Post-Incident Review | Review following a significant security incident | As needed | Incident Response Team | Analyze and adjust for improvements |
| Compliance Review | Regular review to ensure ongoing compliance | Bi-annually | Compliance Officer | Stay updated with regulatory changes |
| Technology Review | Review of technology investments and updates | Annually | IT Manager | Ensure adoption of latest security tech |
| Vendor Review | Assessment of vendor performance and security measures | Annually | Procurement Manager | Maintain strong vendor relationships |
Best Practices and Recommendations
1. Engaging Leadership and Stakeholders
- Importance of Executive Support:
- Secure Commitment: Ensure that top management understands the critical importance of cybersecurity and is committed to providing the necessary resources.
- Board-Level Awareness: Regularly update the board of directors on cybersecurity issues, risks, and the impact of investments.
- Alignment with Business Goals: Align cybersecurity strategies with overall business objectives to demonstrate their value and necessity.
- Communicating the Value of Cybersecurity Investments:
- Use Metrics and Case Studies: Present data and real-world examples to illustrate the ROI of cybersecurity investments. Highlight how these investments prevent costly breaches and downtime.
- Risk Mitigation: Emphasize the role of cybersecurity in mitigating risks that could lead to financial losses, legal issues, and reputational damage.
- Cost-Benefit Analysis: Provide a detailed analysis showing the benefits of proactive cybersecurity measures versus the potential costs of security incidents.
- Building a Security-Conscious Culture:
- Employee Training: Implement comprehensive training programs to ensure all employees are aware of cybersecurity best practices and their role in maintaining security.
- Regular Updates and Drills: Conduct regular security drills and updates to keep security practices fresh in employees’ minds and prepare them for potential incidents.
- Security Champions: Identify and empower security champions within various departments to promote and enforce good security practices throughout the organization.
2. Leveraging External Resources
- Government Resources and Grants:
- Canadian Centre for Cyber Security (CCCS): Utilize resources and guidelines provided by CCCS for building robust cybersecurity frameworks.
- Canadian Internet Registration Authority (CIRA): Access CIRA’s cybersecurity tools and services designed to protect Canadian businesses.
- Funding Opportunities: Explore grants and funding opportunities from federal and provincial governments to support cybersecurity initiatives.
- Industry Partnerships and Collaborations:
- Cybersecurity Forums and Groups: Join industry-specific forums and groups to stay updated on the latest threats and best practices.
- Public-Private Partnerships: Engage in partnerships with other businesses and public entities to share knowledge and resources.
- Information Sharing and Analysis Centers (ISACs): Participate in ISACs to receive and share information about threats and vulnerabilities relevant to your industry.
- Cybersecurity Information Sharing Networks:
- Canadian Cyber Threat Exchange (CCTX): Become a member of CCTX to access threat intelligence and collaborate with other Canadian businesses on cybersecurity issues.
- Global Threat Intelligence: Leverage global cybersecurity information sharing networks to gain insights into international threats and trends.
- Peer Networks: Build relationships with peers in other organizations to share experiences, strategies, and solutions for common cybersecurity challenges.
By following these best practices and recommendations, Canadian businesses can enhance their cybersecurity posture, engage stakeholders effectively, and leverage external resources to build a comprehensive and resilient cybersecurity strategy.
Case Studies and Examples
1. Case Study: Small Business in Retail
- Overview of Cybersecurity Challenges:
- Context: A small retail business with a growing online presence faced increasing cyber threats, including phishing attacks and data breaches.
- Key Issues: Limited budget, lack of in-house cybersecurity expertise, and increasing regulatory requirements.
- Budget Allocation and Implementation:
- Personnel: Allocated $50,000 for part-time cybersecurity staff and employee training programs.
- Technology: Invested $20,000 in advanced antivirus software, secure payment processing systems, and encrypted customer databases.
- Services: Spent $10,000 on managed security services to provide continuous monitoring and incident response.
- Compliance: Allocated $5,000 for regular audits and ensuring compliance with PIPEDA and PCI DSS.
- Results and Lessons Learned:
- Enhanced Security: Significant reduction in phishing incidents and no major data breaches reported.
- Regulatory Compliance: Successfully passed compliance audits, reducing legal risks and building customer trust.
- Employee Awareness: Increased employee awareness and engagement in cybersecurity practices.
- Scalable Model: Developed a scalable cybersecurity model that could grow with the business.
2. Case Study: Medium-Sized Enterprise in Finance
- Overview of Cybersecurity Challenges:
- Context: A medium-sized financial services company faced complex cybersecurity challenges due to sensitive customer data and stringent regulatory requirements.
- Key Issues: High risk of targeted attacks, need for robust data protection measures, and compliance with multiple regulations (PIPEDA, GDPR).
- Budget Allocation and Implementation:
- Personnel: Allocated $200,000 for a dedicated cybersecurity team, including salaries and continuous professional development.
- Technology: Invested $100,000 in comprehensive security solutions, including firewalls, SIEM systems, and encryption technologies.
- Services: Spent $50,000 on cybersecurity consulting services to design and implement a tailored security strategy.
- Compliance: Allocated $30,000 for regular compliance assessments, legal consultations, and obtaining necessary certifications (ISO 27001, SOC 2).
- Results and Lessons Learned:
- Robust Security Posture: Significant improvement in threat detection and response capabilities, with no major incidents reported.
- Compliance Achievements: Successfully achieved and maintained multiple compliance certifications, enhancing customer confidence and business reputation.
- Continuous Improvement: Established a culture of continuous improvement in cybersecurity practices, with regular updates and reviews.
- Business Continuity: Ensured business continuity through effective incident response planning and disaster recovery solutions.
Conclusion
1. Summary of Key Points
- Importance of Effective Cybersecurity Budgeting: Allocating resources strategically to address cybersecurity risks is crucial for protecting sensitive information and ensuring business continuity.
- Understanding Cybersecurity Needs: Conduct comprehensive risk assessments and consider compliance requirements and business-specific considerations to identify and prioritize cybersecurity needs.
- Key Budget Categories: Focus on personnel, technology, services, compliance, and incident response to create a well-rounded cybersecurity budget.
- Strategic Allocation of Funds: Balance proactive and reactive measures, invest in prevention and response, and ensure continuous improvement and flexibility in budgeting.
- Monitoring and Evaluation: Establish performance metrics and regular review processes to evaluate the effectiveness of the cybersecurity budget and make necessary adjustments.
- Best Practices and Recommendations: Engage leadership, leverage external resources, and build a security-conscious culture to enhance cybersecurity efforts.
- Case Studies and Examples: Learn from real-world examples of businesses that successfully allocated their cybersecurity budgets to improve security posture and achieve compliance.
2. Additional Resources
- Government and Industry Guidelines: Utilize resources from the Canadian Centre for Cyber Security (CCCS), Canadian Internet Registration Authority (CIRA), and other relevant organizations.
- Contact Information for Cybersecurity Experts and Consultants: Seek advice from experienced professionals to tailor cybersecurity strategies to specific business needs.
- Templates and Tools for Further Customization: Access additional templates and tools to customize the cybersecurity budget template according to unique business requirements.





