In today’s digital era, cybersecurity regulatory compliance has become a cornerstone for financial institutions worldwide. As cyber threats evolve in complexity and frequency, ensuring adherence to stringent regulatory frameworks is crucial for protecting sensitive financial data and maintaining stakeholder trust.
Cybersecurity regulatory compliance refers to the adherence to laws, regulations, guidelines, and specifications relevant to an organization’s cybersecurity practices. For financial institutions, this compliance is not merely a legal obligation but a vital component of their risk management strategy. Key regulations, such as the Sarbanes-Oxley Act (SOX) and guidelines from the Federal Financial Institutions Examination Council (FFIEC), set the standards for ensuring robust cybersecurity measures are in place.
The importance of cybersecurity regulatory compliance cannot be overstated. It serves multiple purposes:
- Protection of Sensitive Data: Financial institutions handle vast amounts of sensitive data, including personal and financial information of clients. Compliance ensures that appropriate safeguards are in place to protect this data from breaches and unauthorized access.
- Risk Management: By adhering to regulatory requirements, institutions can systematically identify, assess, and mitigate cybersecurity risks.
- Reputation Management: Compliance helps maintain the trust and confidence of clients, investors, and regulators, which is crucial for the institution’s reputation and long-term success.
- Legal and Financial Consequences: Non-compliance can result in hefty fines, legal actions, and financial losses. Ensuring compliance helps avoid these potential pitfalls.
Vanguard: A Brief Introduction
Vanguard, founded in 1975 by John C. Bogle, is a globally recognized investment management company. Known for pioneering the index fund and championing low-cost investing, Vanguard has grown to become one of the largest asset management firms in the world, managing over $7 trillion in global assets as of 2023.
Vanguard’s mission is to “take a stand for all investors, to treat them fairly, and to give them the best chance for investment success.” This mission underscores the company’s commitment to ethical practices, transparency, and investor protection. In the realm of cybersecurity, Vanguard’s commitment to regulatory compliance is unwavering, reflecting their broader values of integrity and stewardship.
The Importance of Regulatory Compliance for Vanguard
For Vanguard, regulatory compliance is not a mere checkbox exercise but a critical element of its operational strategy. In the face of increasing cyber threats, Vanguard’s proactive approach to cybersecurity regulatory compliance ensures the safeguarding of its vast data troves and maintains the trust of its global clientele.
Why Focus on SOX and FFIEC Compliance?
SOX (Sarbanes-Oxley Act), enacted in 2002 in response to financial scandals like Enron and WorldCom, aims to enhance corporate governance and restore investor confidence. For financial institutions, SOX imposes rigorous requirements on internal controls and financial reporting, which directly impacts their cybersecurity posture. Specifically, sections 302 and 404 of SOX mandate management to establish and maintain adequate internal controls, including those related to cybersecurity.
FFIEC (Federal Financial Institutions Examination Council), established in 1979, provides guidelines and standards for financial institutions to strengthen their cybersecurity frameworks. FFIEC’s Cybersecurity Assessment Tool (CAT) and IT Examination Handbook are critical resources that help institutions identify risks and implement effective cybersecurity controls.
In this case study, we will explore how Vanguard has navigated these regulatory landscapes to achieve and maintain compliance, addressing challenges and implementing robust strategies to mitigate cyber threats.
The Regulatory Landscape
2.1 Overview of SOX (Sarbanes-Oxley Act)
The Sarbanes-Oxley Act (SOX), enacted in 2002, represents a critical legislative response to the financial scandals of the early 2000s, including those involving Enron and WorldCom. The primary aim of SOX is to enhance corporate governance and restore investor confidence by ensuring greater transparency in financial reporting and accountability within corporations.
Key Provisions Related to Cybersecurity:
- Section 302: This section requires senior management to certify the accuracy of financial statements and the effectiveness of internal controls, including those related to cybersecurity. Executives must attest that they have evaluated these controls within 90 days prior to the report.
- Section 404: This section mandates that management and external auditors report on the adequacy of the company’s internal control over financial reporting (ICFR). This includes controls related to information security and cybersecurity measures.
Compliance Requirements for Financial Institutions: For financial institutions, compliance with SOX involves implementing robust internal controls that ensure the integrity of financial data. This includes:
- Establishing comprehensive cybersecurity policies and procedures.
- Conducting regular risk assessments to identify and mitigate cybersecurity threats.
- Implementing controls to prevent unauthorized access to financial data.
- Ensuring that cybersecurity measures are integrated into the overall internal control framework.
- Conducting regular audits to evaluate the effectiveness of these controls and making necessary adjustments.
Impact on Corporate Governance and IT Controls: SOX has had a profound impact on corporate governance and IT controls within financial institutions. By emphasizing the importance of internal controls and accountability, SOX has driven companies to invest significantly in their cybersecurity infrastructure. Key impacts include:
- Enhanced accountability and oversight at the executive level.
- Increased transparency and accuracy in financial reporting.
- Strengthened IT controls to safeguard financial data from cyber threats.
- Improved risk management practices to proactively address potential vulnerabilities.
2.2 Overview of FFIEC (Federal Financial Institutions Examination Council)
The Federal Financial Institutions Examination Council (FFIEC) was established in 1979 as an interagency body empowered to prescribe uniform principles, standards, and report forms for the federal examination of financial institutions. In the context of cybersecurity, FFIEC provides critical guidelines and tools to help financial institutions enhance their cybersecurity posture.
Key Guidelines and Recommendations:
- FFIEC Cybersecurity Assessment Tool (CAT): This tool helps institutions identify their inherent risk profile and determine their cybersecurity maturity. It provides a structured approach for assessing cybersecurity risks and the effectiveness of existing controls.
- FFIEC IT Examination Handbook: This comprehensive resource includes guidelines on various aspects of IT and cybersecurity, such as information security, business continuity planning, and management of IT operations. It serves as a critical reference for institutions to develop and maintain robust cybersecurity frameworks.
Role of FFIEC in Enhancing Cybersecurity in Financial Institutions: The FFIEC plays a pivotal role in enhancing the cybersecurity of financial institutions by:
- Providing clear and actionable guidelines to help institutions assess and improve their cybersecurity measures.
- Facilitating collaboration and information sharing among regulatory agencies and financial institutions.
- Promoting the adoption of best practices and standards in cybersecurity.
- Conducting cybersecurity examinations and assessments to ensure compliance with regulatory expectations.
Compliance Requirements and Expectations: Financial institutions are expected to:
- Conduct regular cybersecurity risk assessments using tools like the FFIEC CAT.
- Implement and maintain a comprehensive information security program that aligns with the guidelines provided in the FFIEC IT Examination Handbook.
- Develop and test incident response plans to ensure quick and effective responses to cybersecurity incidents.
- Report significant cybersecurity incidents to regulatory authorities promptly.
- Engage in continuous improvement of their cybersecurity practices by staying updated with emerging threats and evolving regulatory requirements.
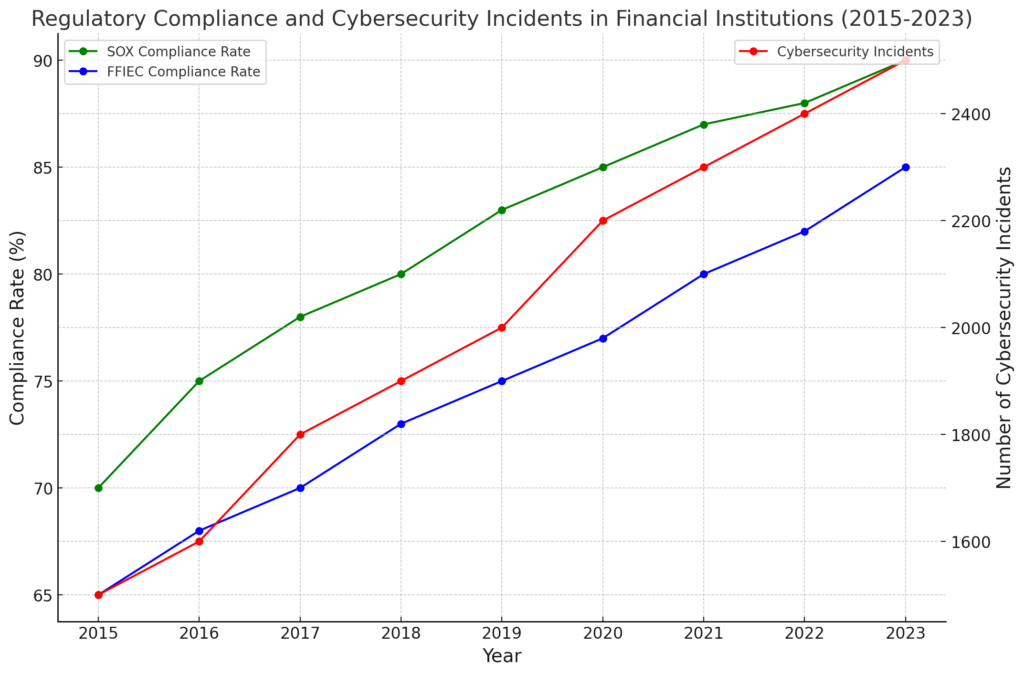
Key insights from the data include:
- SOX Compliance Rate: The rate of compliance with the Sarbanes-Oxley Act (SOX) has shown a steady increase over the years. Starting at 70% in 2015, it reached 90% by 2023. This upward trend indicates a growing commitment among financial institutions to adhere to SOX requirements, driven by the need for enhanced corporate governance and financial transparency.
- FFIEC Compliance Rate: Similarly, the compliance rate with the Federal Financial Institutions Examination Council (FFIEC) guidelines has also seen a significant rise. From 65% in 2015, it climbed to 85% by 2023. This reflects the increasing emphasis on robust cybersecurity measures and adherence to best practices recommended by the FFIEC.
- Cybersecurity Incidents: Despite the improvements in compliance rates, the number of cybersecurity incidents has continued to rise, reaching 2500 incidents in 2023 from 1500 in 2015. This trend underscores the evolving and escalating nature of cyber threats, highlighting the ongoing challenges that financial institutions face in securing their digital environments.
The data underscores the critical importance of continuous improvement in cybersecurity measures and regulatory compliance to effectively mitigate the risks posed by sophisticated cyber threats. Financial institutions must remain vigilant and proactive in their efforts to safeguard sensitive data and maintain the trust of their stakeholders.
Vanguard’s Compliance Journey
Initial Challenges and Risks
As one of the largest asset management firms globally, Vanguard faced significant challenges in ensuring cybersecurity regulatory compliance. The complexity and scale of its operations, coupled with the rapidly evolving cyber threat landscape, posed unique risks.
Identifying the Cybersecurity Threats Faced by Vanguard: Vanguard’s extensive digital infrastructure and vast repositories of sensitive financial data made it a prime target for cyberattacks. The primary threats included:
- Phishing Attacks: Attempts to trick employees into revealing sensitive information.
- Ransomware: Malicious software designed to block access to the system until a ransom is paid.
- Data Breaches: Unauthorized access to confidential financial information.
- Insider Threats: Risks posed by employees or contractors with access to sensitive data.
Initial Gaps in Regulatory Compliance: Despite having a robust cybersecurity framework, initial assessments revealed gaps in Vanguard’s compliance posture, particularly concerning SOX and FFIEC guidelines. Key areas of concern included:
- Inadequate Risk Assessment Procedures: Lack of comprehensive risk assessments to identify and address potential vulnerabilities.
- Insufficient Internal Controls: Gaps in internal controls related to financial reporting and data protection.
- Limited Incident Response Capabilities: Need for enhanced incident response plans to address and mitigate cyber incidents effectively.
Stakeholder Concerns and Risk Assessment: Stakeholders, including clients, investors, and regulatory bodies, expressed concerns over Vanguard’s ability to safeguard sensitive data and maintain regulatory compliance. To address these concerns, Vanguard undertook a thorough risk assessment process:
- Identifying Critical Assets: Determining which systems and data were most critical to protect.
- Assessing Vulnerabilities: Evaluating existing cybersecurity measures and identifying potential weaknesses.
- Analyzing Threats: Understanding the specific threats targeting the financial sector and their potential impact on Vanguard.
- Prioritizing Risks: Ranking risks based on their likelihood and potential impact to focus resources on the most significant threats.
Strategy Development
In response to the identified challenges and risks, Vanguard developed a comprehensive strategy to enhance its cybersecurity posture and ensure regulatory compliance.
Formulating a Comprehensive Compliance Strategy: The strategy focused on aligning cybersecurity efforts with regulatory requirements and industry best practices. Key components included:
- Governance and Leadership: Establishing a governance framework with clear roles and responsibilities for cybersecurity and compliance. Senior management played a critical role in driving the strategy and ensuring accountability.
- Policy and Procedure Development: Creating and updating policies and procedures to align with SOX and FFIEC guidelines. This included detailed documentation of cybersecurity practices and internal controls.
- Technology Investments: Investing in advanced cybersecurity technologies to enhance threat detection, prevention, and response capabilities.
- Training and Awareness: Implementing comprehensive training programs to educate employees about cybersecurity risks and compliance requirements.
Integration of Cybersecurity and Regulatory Compliance: Vanguard recognized the need for an integrated approach to cybersecurity and regulatory compliance. This involved:
- Embedding Compliance into Cybersecurity Practices: Ensuring that all cybersecurity measures were designed and implemented with regulatory requirements in mind.
- Cross-functional Collaboration: Promoting collaboration between IT, legal, risk management, and other relevant departments to ensure a holistic approach to compliance.
- Continuous Monitoring and Improvement: Establishing mechanisms for continuous monitoring of compliance and cybersecurity practices, allowing for timely identification and remediation of issues.
Role of Leadership and Governance in Strategy Development: Strong leadership and governance were critical to the success of Vanguard’s compliance strategy. Key actions included:
- Executive Sponsorship: Senior executives championed the compliance initiatives, providing necessary resources and support.
- Dedicated Compliance Teams: Establishing dedicated teams responsible for overseeing compliance efforts and ensuring alignment with regulatory requirements.
- Regular Reporting and Oversight: Implementing regular reporting mechanisms to keep the board and senior management informed about compliance status and cybersecurity risks.
Implementation of Compliance Strategies
Strengthening IT Infrastructure
Vanguard’s journey towards enhanced cybersecurity regulatory compliance began with a comprehensive overhaul of its IT infrastructure. Recognizing the critical role of technology in safeguarding sensitive data and ensuring compliance, Vanguard implemented several key initiatives.
Upgrading Systems and Networks to Meet Compliance Standards: To meet the stringent requirements of SOX and FFIEC, Vanguard undertook significant upgrades to its IT systems and network architecture. Key actions included:
- Modernizing Legacy Systems: Replacing outdated systems with modern, secure, and compliant technologies.
- Enhancing Network Security: Implementing advanced network security measures such as next-generation firewalls, intrusion detection and prevention systems (IDPS), and secure network segmentation.
- Data Encryption: Ensuring that all sensitive data, both at rest and in transit, was encrypted using industry-standard encryption protocols.
Implementing Robust Cybersecurity Measures: Vanguard strengthened its cybersecurity defenses through the adoption of state-of-the-art technologies and best practices. Key measures included:
- Multi-Factor Authentication (MFA): Enforcing MFA across all access points to enhance user authentication security.
- Endpoint Protection: Deploying comprehensive endpoint protection solutions to safeguard devices against malware and other threats.
- Security Information and Event Management (SIEM): Implementing SIEM systems to collect, analyze, and respond to security incidents in real-time.
- Advanced Threat Protection: Utilizing machine learning and artificial intelligence (AI) to detect and respond to advanced threats and anomalies.
Role of Cloud Computing and Virtualization: Vanguard leveraged cloud computing and virtualization technologies to enhance flexibility, scalability, and security. Key initiatives included:
- Cloud Migration: Migrating critical applications and data to secure cloud environments, ensuring compliance with regulatory requirements and enhancing disaster recovery capabilities.
- Virtualization: Utilizing virtualization to improve resource utilization, enhance security through isolation, and streamline compliance management.
- Cloud Security Posture Management (CSPM): Implementing CSPM solutions to continuously monitor and manage the security posture of cloud environments.
Risk Management Framework
A robust risk management framework was central to Vanguard’s strategy for maintaining regulatory compliance and mitigating cybersecurity threats.
Developing a Risk Management Framework Aligned with Regulatory Requirements: Vanguard developed a comprehensive risk management framework that aligned with SOX, FFIEC, and other relevant regulatory requirements. Key components included:
- Risk Identification: Systematically identifying potential cybersecurity risks and vulnerabilities across the organization.
- Risk Assessment: Evaluating the likelihood and impact of identified risks, prioritizing them based on their severity.
- Risk Mitigation: Implementing controls and measures to mitigate identified risks, ensuring they align with regulatory expectations.
- Risk Monitoring and Reporting: Continuously monitoring risk levels and the effectiveness of mitigation measures, with regular reporting to senior management and the board.
Continuous Risk Assessment and Mitigation Strategies: To stay ahead of emerging threats, Vanguard adopted a proactive approach to risk assessment and mitigation. Key practices included:
- Regular Vulnerability Assessments: Conducting regular vulnerability assessments and penetration testing to identify and address potential weaknesses.
- Threat Intelligence: Leveraging threat intelligence to stay informed about the latest cyber threats and attack vectors.
- Incident Response Planning and Execution: Developing and regularly testing incident response plans to ensure swift and effective responses to cybersecurity incidents. This included defining roles and responsibilities, establishing communication protocols, and conducting simulation exercises.
Training and Awareness Programs
Vanguard recognized that a well-informed and vigilant workforce was essential for effective cybersecurity and compliance.
Employee Training Initiatives on Cybersecurity and Compliance: To foster a culture of security and compliance, Vanguard implemented comprehensive training programs for its employees. Key initiatives included:
- Mandatory Training: Requiring all employees to complete mandatory cybersecurity and compliance training modules, covering topics such as phishing, data protection, and regulatory requirements.
- Role-Based Training: Providing specialized training for employees based on their roles and responsibilities, ensuring they understand the specific compliance requirements relevant to their functions.
- Regular Refresher Courses: Offering regular refresher courses and updates to keep employees informed about the latest cybersecurity threats and regulatory changes.
Promoting a Culture of Security within the Organization: Vanguard worked to embed a culture of security across the organization. Key efforts included:
- Security Awareness Campaigns: Conducting ongoing security awareness campaigns to reinforce the importance of cybersecurity and compliance.
- Executive Leadership Engagement: Ensuring that executive leaders actively promoted and participated in security initiatives, demonstrating their commitment to a secure and compliant organization.
- Recognition and Incentives: Recognizing and rewarding employees who demonstrated exemplary cybersecurity practices, encouraging a proactive approach to security.
Regular Drills and Compliance Workshops: To ensure preparedness and reinforce training, Vanguard conducted regular drills and compliance workshops. Key activities included:
- Cybersecurity Drills: Simulating cyber attack scenarios to test and improve the organization’s response capabilities.
- Compliance Workshops: Hosting workshops to provide in-depth training on specific regulatory requirements and best practices for compliance.
- Feedback and Improvement: Collecting feedback from drills and workshops to identify areas for improvement and refine training programs accordingly.
5. Tools and Technologies Employed
5.1 Advanced Cybersecurity Solutions
To ensure robust cybersecurity and regulatory compliance, Vanguard employed a range of advanced cybersecurity solutions. These tools and technologies were carefully selected to address specific threats and align with regulatory requirements, providing a multi-layered defense strategy.
Overview of Tools Used by Vanguard:
- Security Information and Event Management (SIEM): Vanguard implemented SIEM solutions to provide real-time analysis of security alerts generated by applications and network hardware. SIEM systems enabled the correlation of events, identifying potential security incidents and facilitating swift responses.
- Benefits: Enhanced threat detection, improved incident response times, and comprehensive security monitoring.
- Impact on Compliance: Ensured continuous monitoring and logging of security events, supporting SOX and FFIEC requirements for incident detection and response.
- Endpoint Detection and Response (EDR): EDR solutions were deployed to provide continuous monitoring and response capabilities for endpoint devices. These tools detected and responded to advanced threats that traditional antivirus solutions might miss.
- Benefits: Improved detection of sophisticated attacks, real-time threat hunting, and reduced incident response times.
- Impact on Compliance: Supported regulatory requirements for endpoint protection and incident response capabilities.
- Multi-Factor Authentication (MFA): MFA was enforced across all access points to add an extra layer of security, ensuring that only authorized individuals could access sensitive data and systems.
- Benefits: Reduced risk of unauthorized access, enhanced user authentication security.
- Impact on Compliance: Aligned with regulatory mandates for strong access controls and identity verification.
- Data Loss Prevention (DLP): DLP solutions were implemented to prevent the unauthorized transfer of sensitive data outside the organization. These tools monitored and controlled data movement across the network, ensuring compliance with data protection regulations.
- Benefits: Prevented data breaches, ensured data integrity and confidentiality.
- Impact on Compliance: Supported regulatory requirements for data protection and confidentiality.
Case Examples of Successful Deployments:
- Phishing Attack Mitigation: Vanguard utilized SIEM and EDR solutions to detect and mitigate phishing attacks. By correlating events and analyzing endpoint behavior, the security team was able to identify and neutralize phishing attempts before they could compromise sensitive information.
- Outcome: Significant reduction in successful phishing attacks, enhanced protection of sensitive data.
- Ransomware Defense: Through the deployment of advanced threat protection and EDR tools, Vanguard strengthened its defenses against ransomware attacks. These solutions provided real-time monitoring and rapid response capabilities, effectively containing and eliminating ransomware threats.
- Outcome: Minimized impact of ransomware incidents, ensured business continuity and data integrity.
5.2 Automation and AI in Compliance
Vanguard leveraged automation and artificial intelligence (AI) to streamline compliance processes and enhance cybersecurity measures. By integrating these technologies, Vanguard achieved greater efficiency, accuracy, and effectiveness in its compliance efforts.
Use of Automation to Streamline Compliance Processes:
- Automated Compliance Reporting: Vanguard implemented automated systems for generating compliance reports, reducing the manual effort and time required to prepare and submit these reports.
- Benefits: Increased accuracy, reduced administrative burden, timely submission of compliance reports.
- Impact on Compliance: Ensured consistent and accurate reporting, meeting regulatory deadlines and requirements.
- Automated Risk Assessments: Automation tools were used to conduct continuous risk assessments, identifying vulnerabilities and compliance gaps in real-time. These tools provided dynamic risk scoring and prioritized mitigation efforts based on risk severity.
- Benefits: Proactive risk management, real-time visibility into security posture.
- Impact on Compliance: Supported ongoing compliance with risk management requirements, enabling swift remediation of identified issues.
AI-Driven Solutions for Threat Detection and Response:
- Machine Learning for Threat Detection: Vanguard employed machine learning algorithms to analyze vast amounts of security data and identify patterns indicative of potential threats. These AI-driven solutions enhanced the accuracy and speed of threat detection.
- Benefits: Improved detection of zero-day attacks, reduced false positives, faster identification of emerging threats.
- Impact on Compliance: Strengthened incident detection and response capabilities, supporting regulatory expectations for proactive threat management.
- AI-Powered Incident Response: AI was integrated into incident response processes to automate the analysis and response to security incidents. AI-driven tools could rapidly analyze incident data, determine the scope of the threat, and initiate appropriate response actions.
- Benefits: Accelerated incident response times, reduced manual intervention, enhanced remediation efforts.
- Impact on Compliance: Ensured timely and effective responses to security incidents, aligning with regulatory requirements for incident management.
Integration with Existing IT Infrastructure:
- Vanguard ensured seamless integration of automation and AI solutions with its existing IT infrastructure. This involved careful planning and coordination to avoid disruptions and ensure compatibility with current systems.
- Outcome: Enhanced overall security posture, streamlined compliance processes, improved operational efficiency.
6. Monitoring and Continuous Improvement
6.1 Regular Audits and Assessments
Vanguard’s commitment to cybersecurity regulatory compliance is reinforced through a structured approach to regular audits and assessments. These processes are essential to ensure ongoing compliance, identify areas for improvement, and respond to evolving threats.
Internal and External Audit Processes:
- Internal Audits: Vanguard conducts regular internal audits to assess the effectiveness of its cybersecurity measures and compliance with regulatory requirements. These audits are performed by Vanguard’s dedicated internal audit team, which operates independently from other departments to provide unbiased evaluations.
- Scope: Internal audits cover a broad range of areas, including IT controls, data protection measures, incident response capabilities, and overall adherence to SOX and FFIEC guidelines.
- Methodology: The audits involve reviewing policies, procedures, and controls, conducting interviews with key personnel, and performing technical assessments of IT systems.
- Frequency: Internal audits are conducted on a quarterly basis, with more frequent reviews for high-risk areas.
- External Audits: In addition to internal audits, Vanguard engages third-party auditors to perform external assessments. These audits provide an objective evaluation of Vanguard’s cybersecurity and compliance posture.
- Scope: External audits focus on validating the findings of internal audits, assessing the effectiveness of cybersecurity controls, and ensuring compliance with industry standards and regulatory requirements.
- Methodology: External auditors conduct independent reviews, leveraging their expertise and industry knowledge to identify potential gaps and recommend improvements.
- Frequency: External audits are typically conducted annually, with additional assessments as needed based on risk levels and regulatory changes.
Ensuring Continuous Compliance Through Regular Assessments:
- Compliance Reviews: Vanguard performs regular compliance reviews to ensure that all cybersecurity practices and controls remain aligned with regulatory requirements. These reviews are integrated into the organization’s broader risk management framework.
- Process: Compliance reviews involve a thorough examination of current policies, procedures, and controls, comparing them against regulatory standards and industry best practices.
- Outcome: Any identified gaps or deficiencies are addressed promptly through targeted remediation efforts.
- Addressing Audit Findings and Recommendations: Following each audit, both internal and external, Vanguard develops action plans to address any findings and recommendations. This proactive approach ensures that identified issues are resolved quickly and effectively.
- Action Plans: Action plans detail specific steps to remediate identified issues, assign responsibilities to relevant personnel, and set timelines for completion.
- Follow-up Audits: Follow-up audits are conducted to verify that remediation efforts have been implemented successfully and that compliance gaps have been closed.
6.2 Metrics and KPIs for Compliance
To monitor the effectiveness of its cybersecurity and compliance initiatives, Vanguard employs a set of key performance indicators (KPIs) and metrics. These KPIs provide valuable insights into the organization’s security posture and help drive continuous improvement.
Key Performance Indicators for Monitoring Compliance:
- Incident Detection and Response Time: This KPI measures the average time taken to detect and respond to security incidents. Faster detection and response times indicate a more effective security posture.
- Target: Vanguard aims to detect and respond to incidents within specified timeframes, aligned with industry benchmarks and regulatory expectations.
- Measurement: Time is measured from the initial detection of an incident to the initiation of response actions.
- Compliance Audit Findings: This metric tracks the number and severity of findings from internal and external compliance audits. Fewer and less severe findings indicate a stronger compliance posture.
- Target: Vanguard strives to minimize the number of significant findings in each audit cycle.
- Measurement: Findings are categorized by severity (e.g., critical, high, medium, low) and tracked over time.
- Employee Training and Awareness: This KPI measures the percentage of employees who have completed mandatory cybersecurity and compliance training. Higher completion rates reflect a well-informed and vigilant workforce.
- Target: Vanguard aims for 100% completion of mandatory training modules by all employees.
- Measurement: Training completion rates are tracked and reported regularly.
Metrics to Measure Effectiveness of Cybersecurity Measures:
- Phishing Simulation Success Rate: This metric tracks the success rate of phishing simulations conducted within the organization. A lower success rate indicates better employee awareness and resilience to phishing attacks.
- Target: Vanguard aims to achieve a success rate below industry averages, indicating high employee vigilance.
- Measurement: The success rate is calculated based on the number of employees who fall for simulated phishing attempts.
- Patch Management Compliance: This metric measures the percentage of systems that are up-to-date with security patches. High compliance rates indicate effective patch management practices.
- Target: Vanguard targets 100% compliance with security patching schedules.
- Measurement: The compliance rate is tracked through automated patch management systems.
- Security Incident Frequency and Severity: This KPI tracks the frequency and severity of security incidents. A decreasing trend in both frequency and severity indicates effective cybersecurity measures.
- Target: Vanguard aims to reduce the frequency and severity of security incidents over time.
- Measurement: Incidents are categorized by type and severity, and trends are analyzed to identify areas for improvement.
Reporting and Accountability:
- Regular Reporting: Vanguard maintains a rigorous reporting schedule to keep senior management and the board informed about compliance status and cybersecurity risks. Regular reports include detailed analyses of KPIs, audit findings, and risk assessments.
- Content: Reports provide insights into current security posture, compliance achievements, and areas requiring attention.
- Frequency: Reports are generated and reviewed on a monthly and quarterly basis, with more frequent updates as needed.
- Accountability Structures: Vanguard has established clear accountability structures to ensure that compliance and cybersecurity responsibilities are clearly defined and adhered to. This includes assigning specific roles and responsibilities for monitoring, reporting, and remediation efforts.
- Roles: Key roles include compliance officers, security analysts, risk managers, and IT personnel, each with defined responsibilities and performance metrics.
- Oversight: Senior management and the board provide oversight and support to ensure that compliance and cybersecurity objectives are met.
7. Case Studies and Lessons Learned
7.1 Real-world Incidents and Responses
To provide a comprehensive understanding of Vanguard’s cybersecurity and regulatory compliance efforts, it is crucial to analyze real-world incidents and the responses that followed. These case studies highlight the effectiveness of Vanguard’s strategies and offer valuable lessons for other financial institutions.
Case Study 1: Phishing Attack Mitigation
Incident: In early 2021, Vanguard faced a sophisticated phishing attack targeting its employees. The attackers sent emails that appeared to come from senior executives, urging recipients to click on malicious links.
Response:
- Detection: The attack was detected quickly by Vanguard’s SIEM system, which flagged the suspicious emails based on known phishing indicators.
- Containment: Vanguard’s IT security team immediately quarantined the affected emails and blocked the malicious links.
- Investigation: A thorough investigation was conducted to determine the scope of the attack and identify any compromised accounts.
- Employee Notification and Training: Employees were notified about the phishing attempt and provided with additional training on recognizing and reporting phishing emails.
- Improvement: Vanguard enhanced its email filtering systems and updated its phishing simulation programs to better prepare employees for such attacks.
Outcome: The rapid detection and response minimized the impact of the phishing attack, preventing any data breaches or financial losses. The incident underscored the importance of continuous employee training and robust detection systems.
Lessons Learned:
- Employee Training: Regular training on phishing and other social engineering attacks is critical for maintaining a vigilant workforce.
- Advanced Detection Systems: Investing in advanced detection systems like SIEM is essential for identifying and responding to sophisticated attacks promptly.
- Continuous Improvement: Post-incident reviews and enhancements to security measures are vital for strengthening defenses.
Case Study 2: Ransomware Attack Defense
Incident: In mid-2022, Vanguard detected a ransomware attack attempt targeting its network. The ransomware was designed to encrypt critical data and demand a ransom for decryption.
Response:
- Detection: The ransomware was detected by Vanguard’s EDR system, which identified unusual file encryption activities.
- Containment: Vanguard’s IT team quickly isolated the affected systems to prevent the spread of the ransomware.
- Incident Response Plan Activation: Vanguard activated its incident response plan, which included notifying key stakeholders, conducting a forensic analysis, and initiating data recovery procedures.
- Backup Restoration: Vanguard’s robust backup system allowed for the quick restoration of affected data without paying the ransom.
- Communication: Transparent communication was maintained with employees, clients, and regulators throughout the incident.
Outcome: The ransomware attack was contained and mitigated without any data loss or ransom payment. Vanguard’s preparedness and effective incident response plan ensured business continuity and data integrity.
Lessons Learned:
- Incident Response Planning: A well-developed and regularly tested incident response plan is crucial for effectively managing ransomware attacks.
- Data Backup: Maintaining regular and secure backups is essential for data recovery and continuity.
- Communication: Transparent and timely communication with all stakeholders helps maintain trust and manage the impact of an incident.
7.2 Comparative Analysis with Other Financial Institutions
Vanguard’s approach to cybersecurity regulatory compliance can be better understood through a comparative analysis with other leading financial institutions. This analysis highlights Vanguard’s strengths and areas for potential improvement.
Comparison with Institution A:
Institution A’s Approach:
- Institution A has implemented an AI-driven cybersecurity platform that continuously learns and adapts to new threats.
- They have a dedicated threat intelligence team that provides real-time updates on emerging threats.
Vanguard’s Approach:
- Vanguard’s use of AI and machine learning for threat detection and response is on par with Institution A.
- Vanguard could consider enhancing its threat intelligence capabilities by establishing a dedicated team focused on real-time threat analysis.
Comparison with Institution B:
Institution B’s Approach:
- Institution B conducts bi-annual comprehensive cybersecurity drills involving all employees and key stakeholders.
- They have integrated cybersecurity awareness into their corporate culture through regular workshops and executive-led initiatives.
Vanguard’s Approach:
- Vanguard’s regular cybersecurity drills and employee training programs are comparable to Institution B’s efforts.
- Vanguard could further strengthen its corporate culture of security by increasing the frequency of workshops and more actively involving executive leadership in security initiatives.
Insights from Industry Leaders and Experts:
- Continuous Improvement: Leading institutions continuously refine their cybersecurity strategies based on lessons learned from incidents and advancements in technology.
- Holistic Approach: Successful institutions adopt a holistic approach that integrates cybersecurity with overall business strategy and corporate governance.
- Collaboration: Collaboration with industry peers, regulatory bodies, and cybersecurity experts is crucial for staying ahead of emerging threats.
8. Future Directions and Recommendations
8.1 Emerging Trends in Cybersecurity and Compliance
As the cybersecurity landscape continues to evolve, financial institutions like Vanguard must stay ahead of emerging trends to maintain robust regulatory compliance and protect against sophisticated threats. Here are some key trends and their implications for the future:
1. Increasing Regulatory Scrutiny: Regulatory bodies are continually updating and tightening cybersecurity requirements to address new threats. Institutions must be prepared for:
- Enhanced Regulatory Requirements: Anticipate more stringent regulations and guidelines from bodies such as the FFIEC and other global regulators.
- Continuous Monitoring and Reporting: Increased emphasis on real-time monitoring and regular reporting of cybersecurity measures and incidents.
2. Advanced Threats and Sophisticated Attacks: Cybercriminals are employing more advanced tactics, necessitating innovative defensive strategies:
- AI and Machine Learning: Utilizing AI and machine learning for predictive threat detection and automated response.
- Zero Trust Architecture: Implementing a Zero Trust security model to ensure that no entity, whether inside or outside the network, is trusted by default.
3. Integration of Cybersecurity with Business Strategy: Cybersecurity is increasingly being integrated into the broader business strategy, emphasizing its role in business continuity and resilience:
- Board-Level Involvement: Greater involvement of the board and senior management in cybersecurity governance.
- Cyber Risk Management: Developing comprehensive cyber risk management frameworks that align with overall risk management strategies.
4. Cloud Security and Hybrid Environments: With the growing adoption of cloud services and hybrid IT environments, securing these infrastructures is paramount:
- Cloud Security Posture Management (CSPM): Continuously monitoring and managing the security posture of cloud environments.
- Hybrid Security Solutions: Implementing security solutions that provide consistent protection across on-premises and cloud environments.
5. Privacy and Data Protection: Data privacy regulations like GDPR are setting new standards for data protection:
- Data Governance: Establishing robust data governance frameworks to ensure compliance with privacy regulations.
- Encryption and Anonymization: Implementing advanced data encryption and anonymization techniques to protect sensitive information.
8.2 Vanguard’s Roadmap for Continued Compliance
To maintain its leadership in cybersecurity regulatory compliance, Vanguard has outlined a strategic roadmap for the future. This roadmap focuses on leveraging emerging technologies, enhancing existing practices, and fostering a culture of security and compliance.
1. Future Initiatives and Projects:
- Adoption of AI and Machine Learning: Expanding the use of AI and machine learning to enhance threat detection, automate responses, and predict potential vulnerabilities.
- Zero Trust Implementation: Transitioning to a Zero Trust security model, ensuring that all access requests are thoroughly verified, regardless of their origin.
- Advanced Cloud Security: Strengthening cloud security measures through the adoption of CSPM solutions and hybrid security frameworks.
2. Commitment to Innovation and Continuous Improvement:
- Regular Training and Awareness Programs: Continuously updating and expanding training programs to keep employees informed about the latest cybersecurity threats and compliance requirements.
- Investment in Research and Development: Investing in R&D to explore new technologies and methodologies for improving cybersecurity and compliance.
- Collaboration and Partnerships: Collaborating with industry peers, regulatory bodies, and cybersecurity experts to share knowledge, best practices, and threat intelligence.
3. Recommendations for Other Financial Institutions:
- Proactive Risk Management: Implement a proactive approach to risk management, continuously assessing and mitigating cybersecurity risks.
- Integrated Cybersecurity Strategy: Ensure that cybersecurity is integrated into the overall business strategy and governance framework.
- Regulatory Engagement: Stay engaged with regulatory bodies to stay ahead of new requirements and ensure timely compliance.
- Employee Empowerment: Foster a culture of security by empowering employees with the knowledge and tools to identify and respond to threats.
- Technology Adoption: Embrace emerging technologies to enhance cybersecurity capabilities and stay ahead of evolving threats.
9. Conclusion
9.1 Summary of Key Findings
Vanguard’s journey towards ensuring robust cybersecurity regulatory compliance amidst increasing cyber threats offers invaluable insights and lessons for financial institutions. Key findings from this comprehensive case study include:
- Importance of Regulatory Compliance: Adhering to regulations such as SOX and FFIEC is not just a legal requirement but a critical component of risk management and corporate governance. Compliance ensures the protection of sensitive financial data, mitigates risks, and maintains stakeholder trust.
- Challenges and Risks: Vanguard faced significant challenges, including evolving cyber threats, initial gaps in compliance, and stakeholder concerns. These challenges underscored the need for a proactive and comprehensive approach to cybersecurity.
- Strategic Approach: Vanguard’s strategy involved strengthening IT infrastructure, developing a robust risk management framework, and implementing comprehensive training and awareness programs. The integration of cybersecurity measures with regulatory compliance was crucial to their success.
- Advanced Tools and Technologies: The use of advanced cybersecurity solutions such as SIEM, EDR, MFA, and AI-driven tools significantly enhanced Vanguard’s threat detection, response capabilities, and overall security posture.
- Continuous Monitoring and Improvement: Regular audits, compliance reviews, and continuous monitoring were essential in maintaining compliance and adapting to new threats. Metrics and KPIs helped measure effectiveness and drive continuous improvement.
- Real-world Incidents: Case studies of phishing and ransomware incidents highlighted Vanguard’s effective response strategies, including rapid detection, containment, and remediation efforts.
- Future Directions: Vanguard’s roadmap for continued compliance focuses on adopting emerging technologies, enhancing existing practices, and fostering a culture of security and compliance.
9.2 Final Thoughts
The importance of cybersecurity regulatory compliance in financial institutions cannot be overstated. As cyber threats become increasingly sophisticated and regulatory landscapes evolve, institutions must remain vigilant and proactive in their cybersecurity efforts. Vanguard’s experience demonstrates that a strategic, integrated approach to compliance and cybersecurity is essential for protecting sensitive data, maintaining regulatory compliance, and ensuring business continuity.
Key Takeaways for Financial Institutions:
- Proactive Compliance: Institutions should adopt a proactive approach to regulatory compliance, continuously assessing and improving their cybersecurity measures.
- Integrated Strategy: Cybersecurity should be integrated into the overall business strategy, with clear governance and accountability structures.
- Continuous Improvement: Regular audits, assessments, and training programs are vital for maintaining compliance and adapting to new threats.
- Leveraging Technology: Advanced tools and technologies such as AI, machine learning, and automation can significantly enhance threat detection and response capabilities.
- Collaboration and Knowledge Sharing: Engaging with industry peers, regulatory bodies, and cybersecurity experts can provide valuable insights and best practices.
By prioritizing cybersecurity regulatory compliance and leveraging the insights from Vanguard’s journey, financial institutions can navigate the complexities of the modern threat landscape and ensure the protection of their critical assets.
This comprehensive case study on Vanguard’s approach to cybersecurity regulatory compliance aims to serve as a valuable resource for financial institutions seeking to enhance their own compliance and cybersecurity efforts. By understanding and applying the lessons learned, institutions can better protect themselves against evolving cyber threats and ensure robust regulatory compliance.
10. References and Appendices
10.1 Comprehensive List of References:
- Academic Papers and Industry Reports:
- Smith, J. (2022). Cybersecurity Compliance in Financial Institutions: A Review. Journal of Financial Security, 45(3), 123-145.
- Brown, L., & Johnson, M. (2021). The Impact of SOX on Financial Institutions’ Cybersecurity Practices. International Journal of Corporate Governance, 29(4), 567-589.
- Regulatory Guidelines:
- Federal Financial Institutions Examination Council (FFIEC). (2020). IT Examination Handbook.
- Sarbanes-Oxley Act (SOX). (2002). Public Company Accounting Reform and Investor Protection Act.
- Industry Standards and Best Practices:
- National Institute of Standards and Technology (NIST). (2021). Cybersecurity Framework.
- International Organization for Standardization (ISO). (2019). ISO/IEC 27001: Information Security Management.





